A recurrent metaphor in the annals of warfare is that its “better to shoot the archer, not the arrow”. This line of thinking has led to such tactical and technological innovations over the decades as counter-battery fire, counter-sniper systems, some aspects of offensive counter-air and counter-C4ISR.
However, the nascent counter-drone space has yet to fully embrace the targeting of the controller itself as it’s own CONOPs. Most C-UAS systems on the market today (as I detail below) are focused on shooting down or neutralizing the drone rather than it’s controller - defending against the arrow rather than disabling the archer.
As autonomous systems scale from 1v1 FPV drone engagements to full on autonomous drone swarms being commanded by a single or handful of users, it is essential we develop systems that can trace them to their point of origin and disable or destroy their controllers rather than attacking their link to the drones or the drones themselves. This is a crucial element of what I have referred to in a previous post as SEEN/DEEN - suppression and destruction of enemy emitters and networks.
In this ‘stack I will outline the gap in the solution space, show examples of how this has played out in other domains, give some of the reasons why this is hard and talk about prospective solutions so that we can take out the archer rather than the arrow.
Our National Counter-UAS strategy is basically defensive counter-air, but for drones
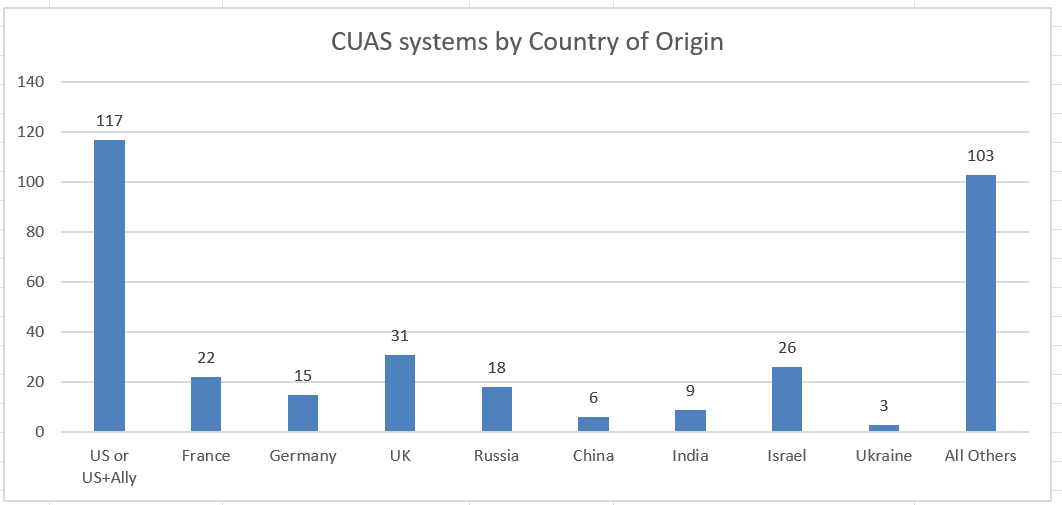
The Global C-UAS buyers guide contains 350 different types of C-UAS systems on the market as of April 2023. This is an insane proliferation of systems for a threat that is less than 15 years old. In Figure 1 below, I’ve binned these systems by their type more broadly to give you an idea of where the action is.

What’s particularly shocking is that for as much investment as Russia, China and Ukraine have invested in UAS technology, there are relatively few CUAS systems (at least ones uncoverable in this research survey). As Figure 2 below shows Russia has 18 systems, China has six and Ukraine has all of three.
It’s likely that some of the underreporting is due to this being an older survey or due to language barrier issues with researching various systems (e.g. Bow of Theseus favorite and Ukrainian friend Unwave was not included in this survey), so let’s treat this more as directionally than precisely accurate. One thing that is clear is that there is a massive proliferation of systems in the US for C-UAS, probably being driven by the rich VC funding and SBIR ecosystems where seemingly every Tam, Dick or Yurii was able to get VC backing or a grant to try something out in the last ten years or so.
Zooming in on the detector space, I read through (ok ChatGPT and I read through) all of them and 90%+ of the solutions are focused on finding and tracking the drone rather than finding the controller, i.e. stopping the arrow not the archer. This is driven by modalities: only SIGINT or Passive RF sensing systems are able to find the drone controller (Radar, Lidar and EO aren’t going to) in any geometry whatsoever since the others are purely meant to find moving targets.
Among passive RF detection systems a few such as AeroDefense, Validrone and Hidden Level do claim to have functionality to detect the drone controller. However, they also openly admit that they are geometrically limited in their ability to do this (i.e. limited by line of sight) and since all of these systems are ground based, this greatly limits their utility.
Line of Sight Challenges
One thing most of us have an intuitive understanding of is just how ineffective we are at spotting things at a distance from ground level. Despite what flat earthers may think, the curvature of the earth ensures that the horizon is barely 3 miles from you with your own eyes. This gets even worse when we couple it with obstacles like terrain, building, trees and other urban detritus which depending on frequency can either attenuate or block transmission entirely.
All but the lowest frequency RF transmissions follow the same line of sight rules as your eyes, so while a drone at a low altitude can be detected a ways off (8-10 miles), a controller’s range of detection is significantly less than that for a ground based transmitter. With kamikaze drones, ISR drones and other systems purporting ranges of 10 miles or more, the controllers are extremely likely to be beyond line of sight for tyour ground based systems to detect them.
Geolocation challenges
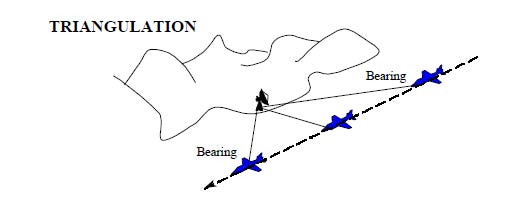
Further compounding the issue of fixing on a controller is that a single fixed RF passive sensor cannot geolocate an emitter on it’s own since it has no ranging capability. It must use either multi-lateration or TDOA techniques in conjunction with multiple sensors that also have line of sight to a ground based controller (see Figure 4). A single emitter can only produce a line of bearing. So to geolocate an emitter, you need multiple assets spread out to do the job and hopefully all of them are within line of sight of the signal of interest

The Obvious Solution: searching for controllers from a drone
Putting an RF detector on a drone solves both the range problem and single ship geolocation problems simultaneously. From even as low of an altitude as 100 feet, the drone would have line of sight of 12 miles or more, well within the range of most controllers. If the controller is expected to be at an even greater range, the drone can also increase it’s altitude until the controller is visible as well or to see over potential obstructions.
In the course of running a search pattern the motion of the drone also allows incredibly accurate geolocation using the same triangulation process, merely along a flight path rather than with multiple sensors. This can be done with relatively low direction finding accuracy thanks to high spatial separation and lots of measurements integrated over time. Figure 5 illustrates how this works.
A drone (or more generally an airborne platform) is the ideal platform for this mission because of the ability to dynamically search for the archer, rather than shooting down the arrow, thereby taking the fight to the enemy. In this respect, it fits in well with how heritage doctrine for fighting air wars applies in the lower altitude, lower speed drone fight in today’s air littorals.
Tying this together with the concept of offensive counterair operations
Offensive and defense counterair historically are a major focus area for the air force. Indeed, much of the electronic warfare enterprise - such as Anti-Radiation Missiles and Stand Off Jamming - is built to conduct several of the sub missions underneath the Offensive Counterair framework shown in Table 2.
The Suppression of Enemy Air Defense and Attack Operations missions have parallels in the Air Littorals domain where today’s “Drone Wars” are taking place. Specifically, it’s attacking a family of communications and EW systems, C2 centers and logistics targets: drone controllers, FPV operators themselves and drone storage & launch facilities (Attack Operations); enemy C-UAS jammers, UAS detection systems such as radars, counter-PNT systems like GPS jammers (SEAD/DEAD). I broadly categorize the latter under the umbrella of Suppression and Destruction of Enemy Emitters and Networks (SEEN/DEEN). There is some overlap with attack operations as drone controllers are essentially C2 nodes, hence why SEEN/DEEN is a more appropriate label for this concept of operations.
Increased complexity in the spectral environment
As counter UAS systems have advanced, so have their counter-counter measures. In particular the datalinks themselves have adopted a number of very hard to counter techniques - known as anti-jam (AJ) technology to counter the increasing number of jammers and detectors out to target these radios.
These techniques aren’t novel: electronically scanned beams and adaptive beamforming; frequency hopping spread spectrum waveforms; power control; interference cancellation algorithms and reserved frequency bands have been known and deployed in many radio systems since at least the 1970s. What is novel now is that these techniques are readily available at commercial price points and scales (down to low thousands or even hundreds of dollars per shipset) due to the ubiquity of modern software defined radios. These technologies are table stakes in the Degraded, Denied, Intermittent and Low Bandwidth (DDIL) environments we are seeing for autonomous systems on the modern battlefield.
I’m going to briefly touch on a few of the more novel solutions not mentioned in the list above.
A word about tethered drones
One anti-jam solution that’s been getting a lot of attention lately is tethered drones. It’s simply impossible to jam a wired signal, so in some ways this is the ultimate anti-jam solution. Tethering involves taking a massive spool of fiber optic cable and unwinding it behind the drone to maintain datalink. Many drones also include the ability to wind the tether back up as it gets closer to the controller.
The Russians have started using this in regions where jamming signals are too dense and impractical to overcome to target high value or high priority targets as shown in the video below.
This solution isn’t a new one: the US Army first fielded the TOW (Tube-launched, Optically tracked, wire-guided) missile in 1968 during Vietnam. It also comes with some real costs and headaches: in addition to the serious weight hit, it limits maneuverability as the drone is now dragging a tether that can snag on obstacles or be inadvertently cut by other airborne targets or explosions, rendering the drone useless. It’s really best utilized in straight shot scenarios on relatively open terrain. However, given the relative simplicity of this approach, it’s likely to continue showing up on battlefields in the future in some capacity or another.
Relay drones
As the battlefield has grown more complex in Ukraine, with counter-UAS jammers degrading data links becoming ubiquitous, and weapon engagement zones (WEZ) for drones frequently exceeding 10-25 km or more from their controllers - more elaborate schema have emerged for ensuring a communications link.
Relay drones have become one popular option for this. This is not a new concept: systems like the Battlefield Airborne Communication Node (BACN) has been in operation for quite some time for more conventional communications. What is new is their low-cost and consumer scale implementation as part of drone warfare, including satcom integration.

Perhaps the most famous of these is the Ukrainian Vampire drone built by Skyfall, also known to the Russians and the world as the Baba Yaga (after a witch that ate children from Slavic folklore). Thousands of these have deployed on the battlefield and with 15 kg of payload capacity they are used for everything from laying down anti-tank mines to acting as light bombers.
The Vampire can also act as a relay to its controller for smaller drones it launches like precision guided missiles via an on-board Starlink terminal. The Starlink terminal is much more difficult to detect and jam than a typical radio link due to it’s higher directivity (beam “pointiness”), more robust waveform control and multiple satellites to connect a link through.
Another advantage beyond greater range is that by moving the direct radio link to the kamikaze drone closer to the target, it increases link margin and becomes more robust against enemy jamming, improving terminal guidance in FPV mode. For instance, if the link distance is cut from 3 km down to 300 m, all things being equal, it takes 100 times the effective radiated power (ERP) to jam the same link. This is a massive advantage on a battlefield where jamming output power is generally limited by the lug ability of the batteries that power the jammer.
By switching the long distance link to Starlink rather than a radio link, the controller becomes somewhat harder to detect for the reasons above. However, detecting it isn’t impossible either. The Russians recently rolled out a “Starlink killer” of their own called the Kalinka system that is able to track Starlink signals and presumably direct fires on them. Many users have started running long cables to the terminals to offset from the drone pilot, since losing an offset antenna is vastly preferable to losing a human controller.
Mobile Ad Hoc Networks
Many modern radio datalink manufacturers such as Persistent Systems, Doodle Labs and Silvus Technologies include the ability to create mobile ad hoc networks (MANETs) of multiple drones or base station controllers. Depending on available topologies and software, these can be single string daisy chains enabling range extension or robust multi-node networks like those shown in Figure 6. The multi-node networks allow such novel capabilities as being able to route signals around nodes that find themselves in regions of high jamming, ensuring long distance signals find their way to their desired final source.
These networks are much harder to map and characterize then simple 1v1 systems, especially as the number of nodes increases. The Silvus SL5200 radio claims scalability to as many as 550 nodes, making mapping the network - somewhat necessary to find the controller - exponentially more difficult than the 1v1 scenario we introduced above.
It’s not clear if anyone has a solution for mapping MANET networks effectively at the physical signal level yet. Perhaps at the cyber level some clues could be uncovered by reading packet headers or similar techniques at the datalink layer of the OSI stack. Some work clearly needs to be done here to have a chance at uncovering controllers in the 1 v many scenarios we are likely to face as the Chinese prepare to field massive drone swarms.
Again, these mobile ad hoc network concepts are nothing new under the sun: Cooperative Engagement Capability, the exquisite version of MANET became a program of record for the US Navy in 1992. What has changed is the cost and consumer availability of these systems. By tying them to thousands of hard to detect and engage nodes, the scale of the program has become vastly more difficult.
Bringing it all together
It’s all too obvious that shooting the archer is better than shooting the arrow. In the drone wars of the 21st century, this is a much more effective way of neutralizing a threat since many hundreds of drones can be targeted by a single source.
For the 1v1 scenarios currently the baseline for FPV kamikaze drones and similar first generation UAS threats, moving our SIGINT capabilities to drones that can pull a “drag net” over the battlefield to fingerprint and fix on any drone controllers of interest, on which fires can then be directed, makes a lot of sense (nota bene: this is part of our current development focus at CX2).
As complex MANET network communications and relays become pervasive, it will become increasingly necessary to use multiple drones to more precisely and rapidly observe and fingerprint the network signals behavior. This means moving beyond SIGINT into what up until now were niche disciplines such as Foreign Instrument Signals Intelligence (FISINT) and Measures and Signals Intelligence (MASINT) and bringing them to the tactical edge.
In conclusion, the ubiquity of complex communication technologies at consumer scale mean that we must develop Find-Fix-Finish capabilities on steroids to counter them.








Nathan, you are right with your focus on the archer! A lot of what you say feels like vindication 😊 Nathan, I think very few people have addressed this on a theoretical, design, and implementation level. I hope more people pay attention. Long time ago when I tried to address the issues you raised I had a hard time. I would have to check, but Mesmer(C-UAS system I co-invented circa 2007) was designed to go after the target directly or, with most drones, the controller/Archer. If I recall correctly, the initial approach detected the signal between the device and controller by using various methods and then attacked, mainly using protocol manipulation, to subvert the device. In some cases, we got the controller to give an estimated location or location from the controller's phone. We developed almost all of our approaches to go after the controller, but we still had issues with the line of site.
As you write about locating your target, we had a hard time with this, We did have a perfect, undeployed solution similar to yours. We developed a few related patents that solved some of the issues of finding control and support systems for drones. I think this patent focuses just on the relay but worked well for our purposes, Airborne relays in cooperative-mimo systems: https://patents.google.com/patent/EP3328733A4/en, was the direction we used for finding the controllers. We did not focus on hard kills; we did more cyber for mitigation and exploitation. There are a lot of problems in this space, as you point out, but it is necessary and has to move on to other forms of dealing with controllers, such as on the ground, in a vehicle, in a drone managing drones, and so on. Also, there is a need to deal with the controller when it’s an AI, or it’s the device's autonomous system. That’s what worries me and what my current research is all about.